What We Do
thentication techniques based on fixed targets can be compromised from threats such as privileged insiders, infected malware and phishing attacks. Any compromise may remain undetected and difficult to recover, creating significant vulnerabilities.
With CASQUE, keys are changed dynamically and invisibly, removing fixed targets and hence becoming immune to insider attacks, token clones and manufacturer compromise.
In the terminology of US National Institute of Standards and Technology Digital Authentication Guidelines, CASQUE fulfils the description of a “Multi-factor Cryptographic Hardware Device able to address Assurance Requirements at “Level 3”- the highest level
CASQUE SNR
CASQUE is fully self-contained with US and EU Patent Protection and has the capability to be scaled to large user numbers without performance degradation.
CASQUE works on any Client Operating System, on any screen, anywhere – even where mobiles are banned.
CASQUE not sensitive to Quantum Computer attacks.
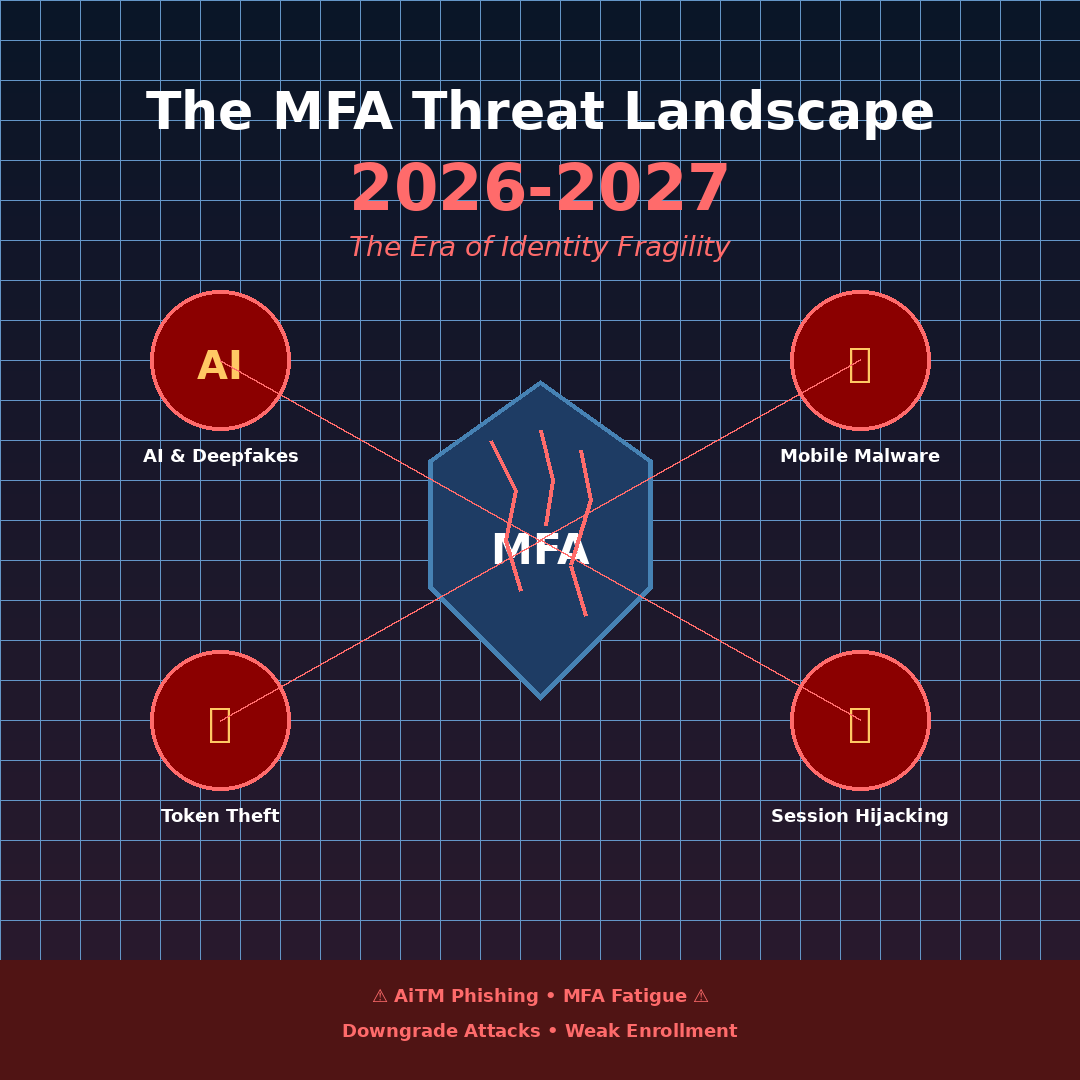
MFA Authentication Landscape 2026 and 2027
The consensus among major research firms (Gartner, NIST, Thales) is that we are entering an era of “Identity Fragility,” where the existing vulnerabilities in MFA Authentication methods are being industrialized by increasingly sophisticated and more easily usable deep fake AI tools.
This is compounded by global political uncertainty with the incentive for antagonistic nation states to sponsor offensive Cyber-attacks.
Multi-factor authentication (MFA) will remain essential over 2026–2027, but attackers are already bypassing it at scale by exploiting the seams around tokens, devices, enrolment, and users rather than breaking the underlying cryptography. ***Click Here for the White Paper ***
Our Partners
CASQUE SNR is delivered via Distributed Management Systems directly or through its accredited System Integrators; it is not provided through any other channel.

